Problem: AD integration fails with error "Error initializing SSL/TLS". How can I set up a secure connection between the AD machine and the Kaseya server for EMM communication using self signed certificate?
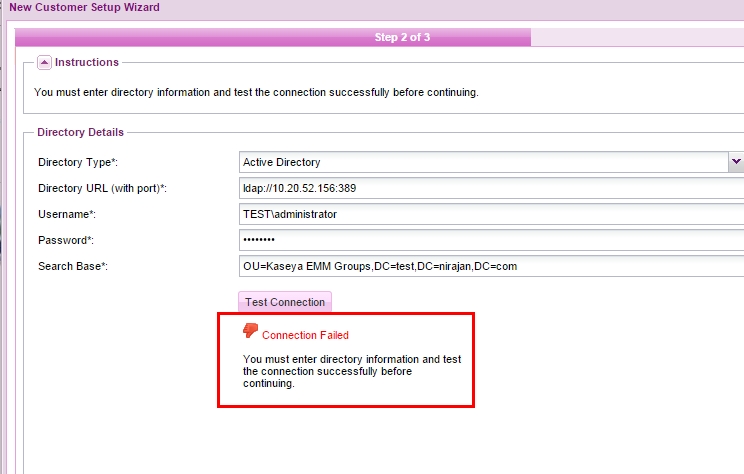
Note: Kaseya Directory Integration Service log available at C:\Kaseya\Logs\Services\directory-webservice.log of Kaseya Server will have an entry like shown below:
ERROR [2015-02-24 03:16:20,324] com.kaseya.directory.core.exceptions.LdapBindFailureException: Bind failed to the LDAP server.
! com.unboundid.ldap.sdk.LDAPException: 00000000: LdapErr: DSID-0C090E17, comment: Error initializing SSL/TLS, data 0, v1db1
! at com.kaseya.directory.core.connection.ConnectionTarget.<init>(ConnectionTarget.java:58) ~[kaseya-directory-integration.jar:na]
! ... 56 common frames omitted
! Causing: com.kaseya.directory.core.exceptions.LdapBindFailureException: Failed to create connection with given config
Resolution: EMM uses StartTLS extended operation to encrypt the communication. This extended operation encrypts the communication channel using SSL/TLS protocol depending upon what’s supported by server/client. Although Kaseya recommends to have TLS client protocol enabled on the AD server, older algorithm i.e SSL 2.0 is still supported - https://www.fastmail.com/help/technical/ssltlsstarttls.html
It is a requirement that AD Server should have at least SSL protocol enabled and a self signed certificate applied.
To verify if SSL is enabled or not, please check the value for:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\SSL 2.0\Client\DisabledbyDefault (1 is enabled and 0 is disabled)
There is a link at the bottom of this article on how to enable Transport Layer Security (TLS) protocol. Please note that SSL and TLS are just sets of protocols but you will still require a certificate to digitally bind a cryptographic key.
This article will give a brief idea on how to use self signed certificate(applies to both SSL and TLS).
Below are few options that you can use to set up self signed certificate on the AD Server:
Option A: Using IIS. The advantage of this option is that self signed certificate created this way will automatically be tagged as trusted root certificate (recommended) - steps 1-7 from this other KB article.
Step 1: Please install IIS on your AD machine from Server Manager > Add roles
- http://www.iis.net/learn/install/installing-iis-7/installing-iis-7-and-above-on-windows-server-2008-or-windows-server-2008-r2
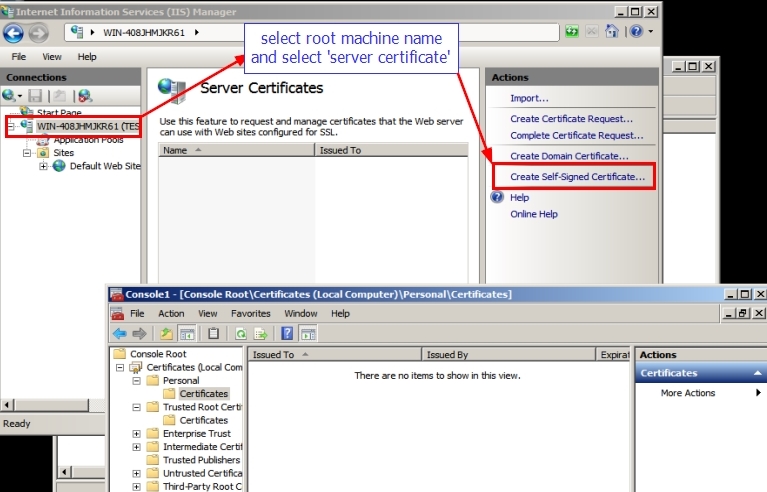
Step 2: In IIS Manager > browse to root server name > double click server certificate > select the option to create self signed certificate:
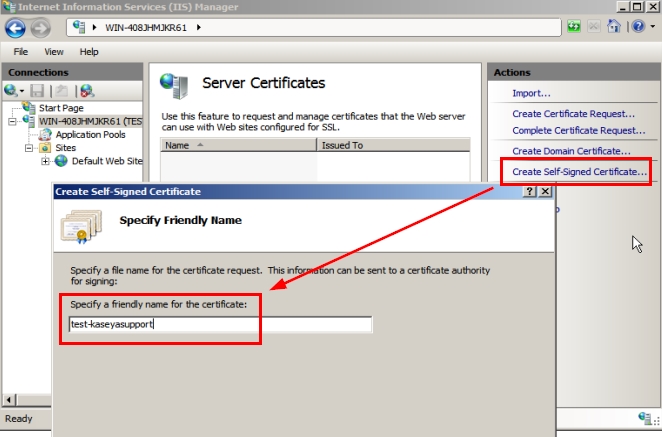
Step 3: Please provide a friendly name for your SSL certificate:
Step 4: You can verify from your Management Console for certificates that the created certificate is now under trusted root certificate or not.
Option B: Using SelfSSL utility:
Instruction is provided in this below article. Please make sure you have this certificate in trusted root:
- http://www.howtogeek.com/107415/it-how-to-create-a-self-signed-security-ssl-certificate-and-deploy-it-to-client-machines/
Note: You can use a digitally signed certificate if you have one available:
- https://support.godaddy.com/help/article/4801/installing-an-ssl-certificate-in-microsoft-iis-7
Here is a link on how to enable TLS protocol if you do plan to use TLS over SSL:
- https://support.quovadisglobal.com/KB/a433/how-to-enable-tls-12-on-windows-server-2008-r2.aspx
- http://tecadmin.net/enable-tls-on-windows-server-and-iis/
More reference:
- http://blogs.msdn.com/b/kaushal/archive/2011/10/02/support-for-ssl-tls-protocols-on-windows.aspx
Option C: For advance users, you can try steps as suggested in below link(Reference/Credit: DigiCert):
Applies to: VSA 9.0, 9.1, 9.2, 9.3, 9.4.