Starting with release 9.5.8, VSA communication layers have been updated to comply with FIPS 140-2 certification, but this requires that a compliant SSL certificate is used. This will be validated during the installation process. If the certificate is invalid, you will have the option to disable FIPS-mode in Edge Services and continue, or to change the certificate.
The attached validation tool can be used to manually validate the certificate prior to installation.
To validate the existing VSA certificate
- Download the attached file ValidateCert.exe to the VSA server.
- From Windows command shell, type the following command:
ValidateCert.exe /validate-existing
- If SSL cert is not FIPs compliant you will see the following message: “Certificate is not FIPS 140-2 compliant”
- If SSL cert is FIPS compliant you will see: “Certificate validated successfully and is compliant”
To validate an external certificate
Use this option to validate an external certificate which has not yet been installed to VSA. You will need to specify the file path and passphrase.
- Download the attached file ValidateCert.exe to the VSA server or another computer where the certificate is saved in a .PFX file.
- From Windows command shell, type the following command:
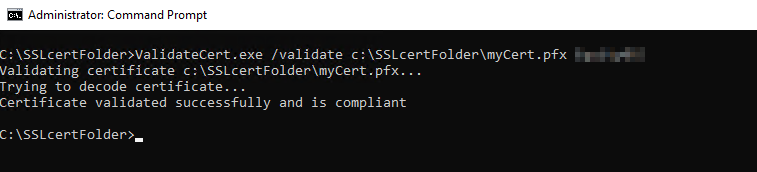
ValidateCert.exe /validate {path_to_SSL_cert} {SSL-cert_password}
For example, ValidateCert.exe /validate c:\SSLCertFolder\myCertificate.pfx myStrongPassword
- If SSL cert is not FIPs compliant you will see the following message: “Certificate is not FIPS 140-2 compliant”
- If SSL cert is FIPS compliant you will see: “Certificate validated successfully and is compliant”
- If another message is returned, the passphrase may be incorrect or path to a valid certificate file was not provided.
Non-compliant certificates
If the certificate is reported as "not compliant", it means the certificate could not be loaded in FIPS mode. This is typically because a non-compliant Cipher such as RC2 is used. To address this, contact the certificate vendor to request a FIPS 140-2 compliant certificate or take the option to disable FIPS mode during VSA installation.
For further information about non-compliant certificates, please refer to this KB article.