Passly supports the use of the Windows Logon agent to enforce 2FA on Windows Logons. The Agent can be deployed to either Stand-alone or Domain joined Windows Servers / Laptop / Desktops / Workstations.
Passly User Accounts
In order to use this functionality the Passly username or alternate username must be an exact match in both Windows and Passly.
Example:
- Windows Username: Redpanda\Administrator
- Passly username: Administrator
Note: Windows Logon agent authentication only validates the username portion and not the domain for 2FA enforcement.
See these guides for help with Passly user accounts.
- How do I add a user? - https://helpdesk.kaseya.com/hc/en-gb/articles/4407400832017
- Creating an Alternative Principal Name (APN) - https://helpdesk.kaseya.com/hc/en-gb/articles/4407393209361
Domain Joined machine logins
When logging into a Domain joined machine, Domain users are expected to enter their Domain username & password before they will be prompted for 2FA. This agent can also support a login using an override password. The Windows Username/Password is verified with Windows before Passly engages.
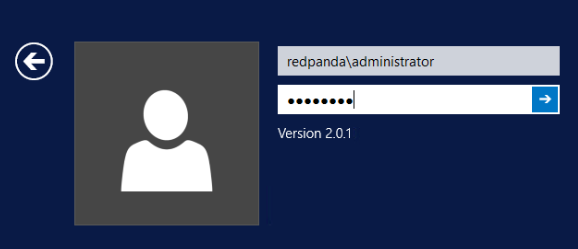
Windows Domain user example
- Domain username: administrator
- Domain Password: password
- Domain: redpanda
Stand-Alone Windows machine logins
When logging into a Stand-alone Windows machine, Users are expected to enter their Windows username & password before they will be prompted for 2FA. This agent can also support a login using an override password. The Windows Username/Password is verified with Windows before Passly engages.
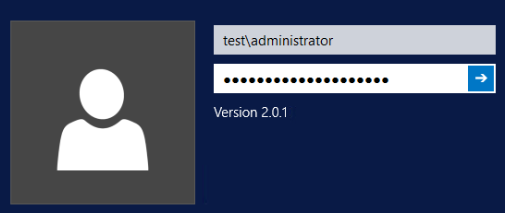
Standalone Windows User Example
- Local Windows username: administrator
- Local Windows password: password
-
Local Windows Name: Test
Additional Resources
- Deploying a Windows Logon Agent - https://helpdesk.kaseya.com/hc/en-gb/articles/4407396797585
- Windows Logon Agent Bulk Deployment https://helpdesk.kaseya.com/hc/en-gb/articles/4407395793169