Background
In August 2021, Kaseya added a new method for authenticating to REST API called Personal Access Token (PAT). PAT is an entity that can be created for each user in VSA, and will be used as credentials for authentication to API. This brings several security benefits: -
- a unique token is used to access the API, which is more secure than a typical user's password.
- unlike a password, the token can only be used to access the API.
- the token can be given more restricted Role access rights than the user it belongs to, based on specific API calls required for the application.
- the token can be restricted by IP address.
This article describes steps to migrate from Basic to TAP authentication method.
Terms
PAT: Personal Access Token (new authentication method for REST API)
Basic Authentication: legacy authentication method using VSA username + password.
How to create PAT and its security settings
1. go to System > User Security > Users, select the user account, click on Access Tokens tab
2. create token with REST API scope and specify its access rights (or it can be configured to inherit from User role)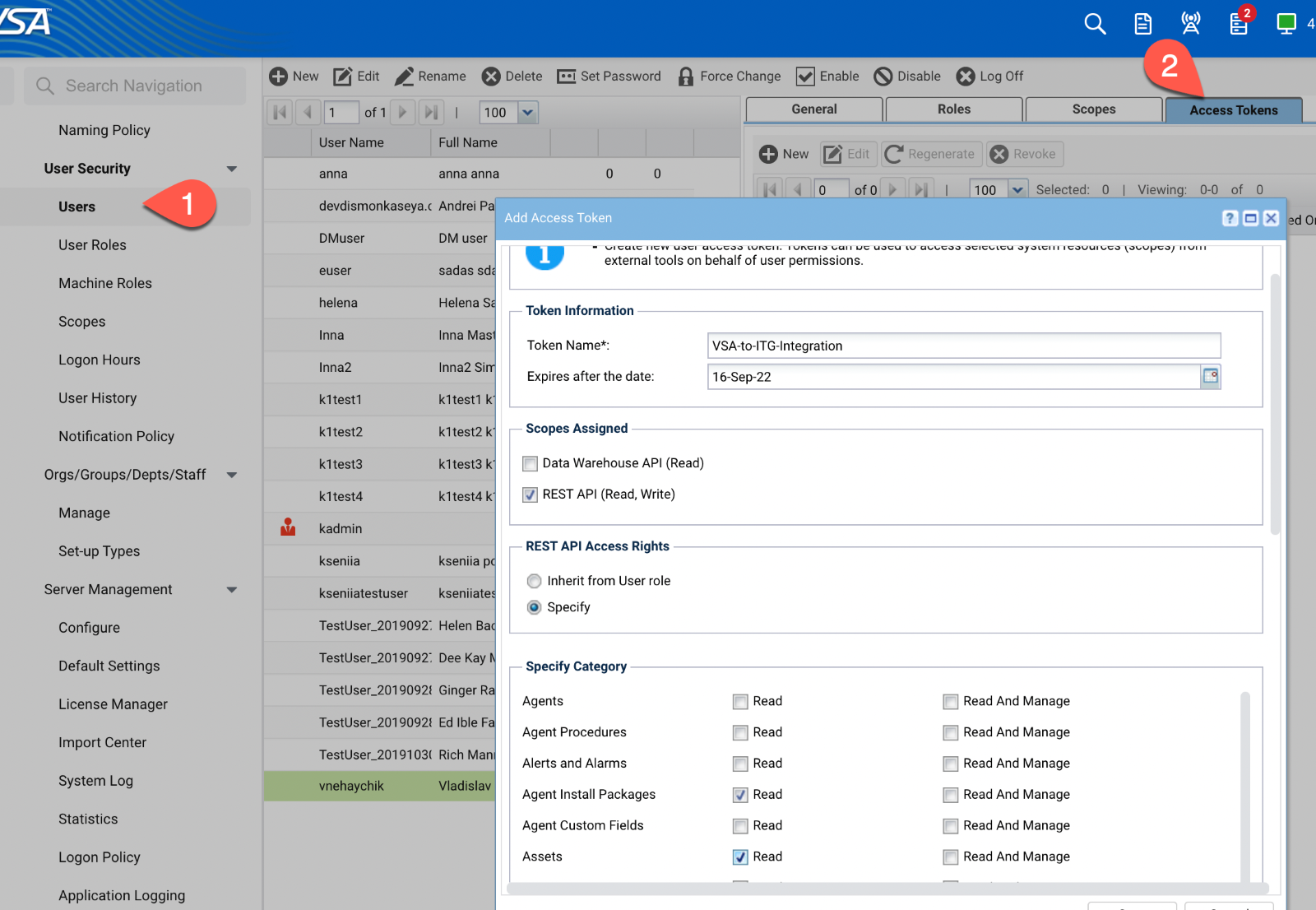
3. specify IP addresses where token is authorized to connect from (leave whitelist empty for unrestricted)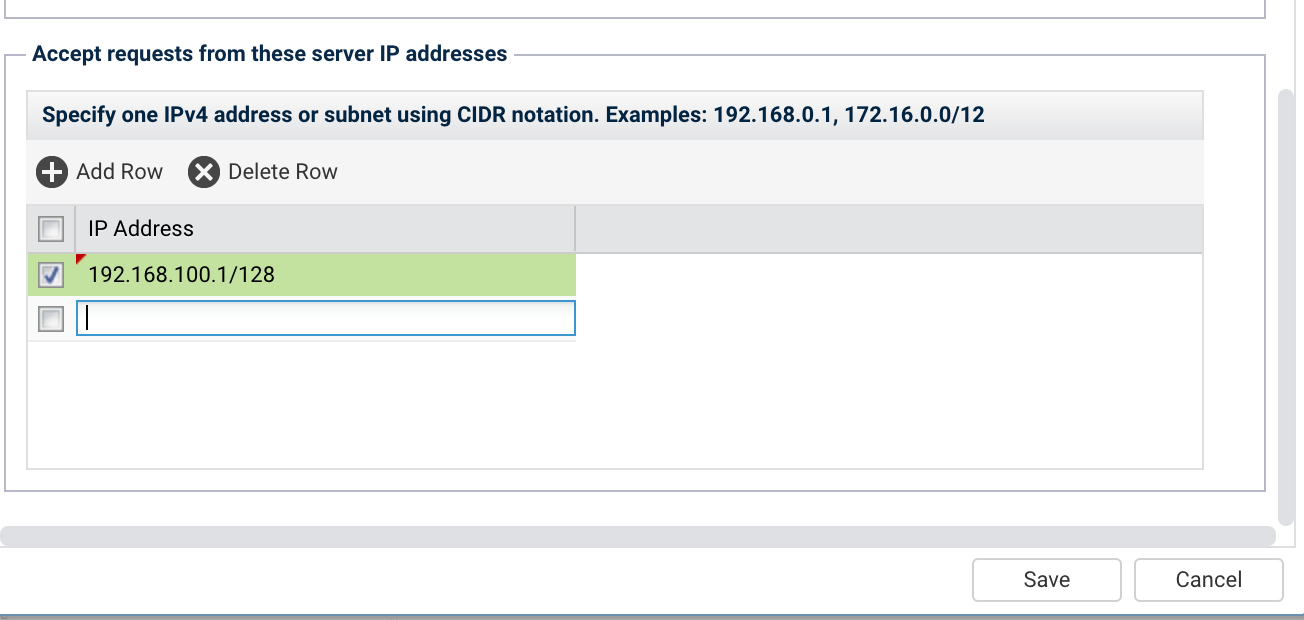
When you save it, a GUID is displayed that will be the token value. When you authenticate to REST API, you will use the username (of the user you generated PAT for) and the GUID as a token. 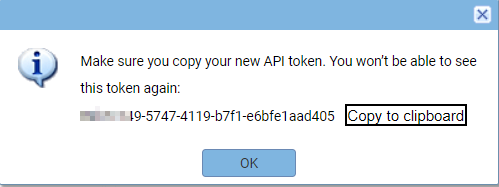
How to authenticate with the PAT
To authenticate to the VSA API you need to get an access token that it is used for a header for each API request. It is the same for both Basic and PAT authentication, so you should not change anything except the method that generates the access token. The code implementation sample is provided on this page: https://help.kaseya.com/webhelp/EN/RESTAPI/9050000/#37334.htm