Issue
A Time of Check & Time of Use (TOCTOU) flaw exists within the VSA Agent on the endpoint where a user can take advantage of a race condition, which could result in executing code with system privileges. The likelihood of practical exploit is low. This flaw cannot be executed remotely and requires that an attacker has already compromised the underlying machine gaining local control of the endpoint with the ability to execute their own code.
Resolution
Step 1 - Update your VSA to the latest patch following the steps highlighted here.
- R9.3 or earlier – Upgrade to R9.4.0.37 or R9.5.
- R9.4 – Install patch 9.4.0.37 or higher.
- R9.5 – Not affected.
Note: For Kaseya SaaS customers, no action is required; our SaaS instances are already on R9.5.
After the patch, a new subdirectory is created in the Agent Working Directory called “System” which only the SYSTEM context and Administrators group have Modify and Write permissions to. Standard users have Read and Execute only. All Kaseya binaries that are executed on a recurring basis from the working directory will now be executed from the System folder.
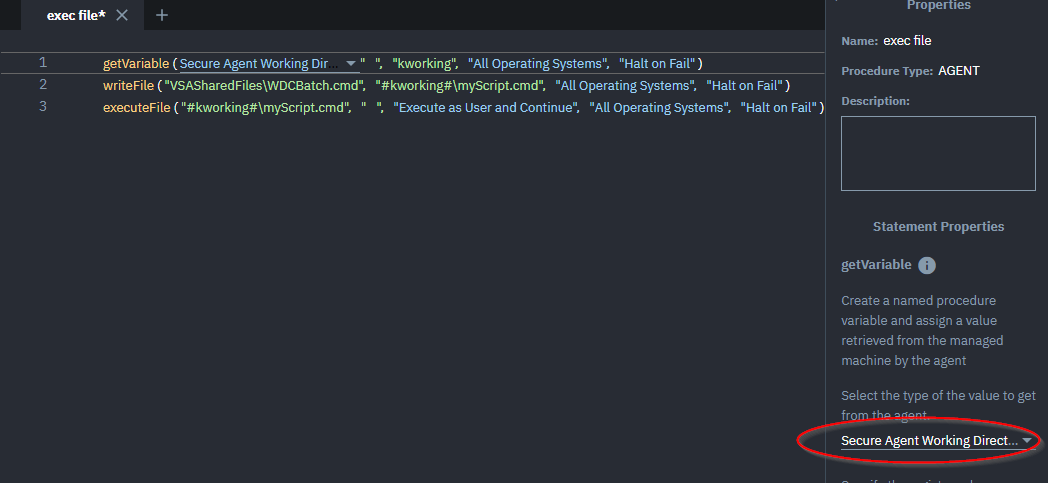
Step 2 – ensure that custom Agent Procedures execute files from a secure location.
Update any custom Agent Procedures that execute files under System context, or as an elevated credential, from the working directory or other non-secure folder, to use the System folder. If a variable is used to define the file path, it can be changed to use the System folder by changing the value type in getVariable() step from “Agent Working Directory” to “Secure Agent Working Directory”.
Applies to: VSA Version 9.4.0.36 and earlier.